
Aug 07, · It find its use in simulating routing protocols like IP, TCP, UDP etc. It creates a simulation environment for studying the network. The steps followed when creating a Students enrolled in the master’s program in computer science at the University of Ottawa may be eligible to fast-track directly into the doctoral program without writing a master’s thesis. For additional information, please consult the “Admission Requirements” section of the PhD program High speed protocols. Mobile IP; Network design and optimization; QoS assurance protocols; This program requires 33 semester credit hours, with both thesis and non-thesis options. Part-time students are enrolled in the non-thesis option to begin but can apply to do the thesis if desired. The thesis is mandatory for most full-time students
10 Best Master’s Programs in Telecommunications
Dernières mises à jour en lien avec la COVID disponibles ici. Latest information about COVID available here. Offered by: Computer Science Faculty of Science. Instructors: Maheswaran, Muthucumaru Fall Maheswaran, Muthucumaru Winter. Computer Science Sci : Exposure to ongoing research directions in computer science through regular attendance of the research colloquium organized by the School of Computer Science.
Complementary courses must satisfy a Computer Science breadth requirement, with at least one course in two of the Theory, Systems, and Application areas. Areas covered by specific courses are determined by the Computer Science graduate program master thesis routing protocols. Computer Science Sci : State-of-the-art language-based techniques for enforcing security policies in distributed computing environments.
Static techniques such as type- and proof-checking technologyverification of security policies and applications such as proof-carrying code, certifying compilers, and proof-carrying authentication. Prerequisites: COMPCOMP Computer Science Sci : Propositional logic - syntax and semantics, temporal logic, other modal logics, model checking, master thesis routing protocols, symbolic model checking, binary decision diagrams, other approaches to formal verification.
Terms: This course is not scheduled for the academic year. Instructors: There are no professors associated with this course for the academic year. Prerequisites: COMP and COMP Computer Science Sci : Introduction to modern constructive logic, its mathematical properties, and its numerous applications in computer science.
Restriction: Not open to students who have taken COMP Computer Science Sci : Models for sequential and parallel computations: Turing machines, boolean circuits. The equivalence of various models and the Church-Turing thesis. Unsolvable problems.
Model dependent measures of computational complexity. Abstract complexity theory. Exponentially and super-exponentially difficult problems. Complete problems. Computer Science Sci : Designing and programming reliable numerical algorithms. Stability of algorithms and condition of problems. Reliable and efficient algorithms for solution of equations, linear least squares problems, the singular value decomposition, the eigenproblem and related problems.
Perturbation analysis of problems. Algorithms for structured matrices. Prerequisite: MATH or COMP Computer Science Sci : This course presents an in-depth study of modern cryptography and data security. The basic information theoretic and computational properties of classical and modern cryptographic systems are presented, followed by a cryptanalytic examination of several important systems.
We will study the applications of cryptography to the security of systems. Prerequisites: COMP or COMPMATH Computer Science Sci : Algorithmic and structural approaches in combinatorial optimization with a focus upon theory and applications.
Topics include: polyhedral methods, network optimization, the ellipsoid method, graph algorithms, matroid theory and submodular functions. Prerequisite: Math or COMP or equivalent. Restriction: This course is reserved for undergraduate honours master thesis routing protocols and graduate students.
Not open to students who have taken or are taking MATH Computer Science Sci : Foundations of game theory. Computation aspects of equilibria. Theory of auctions and modern auction design. General equilibrium theory and welfare economics. Algorithmic mechanism design. Dynamic games. Prerequisite: COMP or MATH or MATH master thesis routing protocols MATHor instructor permission. Restriction: Not open to students who are taking or have taken MATH Computer Science Sci : The theory and application of approximation algorithms.
Topics include: randomized algorithms, network optimization, linear programming and semi definite programming techniques, the game theoretic method, the primal-dual method, and metric embeddings. Prerequisites: COMP or MATH master thesis routing protocols permission of instructor. Computer Science Sci : Algorithms for connectivity, partitioning, clustering, colouring and matching. Isomorphism testing.
Algorithms for special classes of graphs. Layout and embedding algorithms for graphs and networks. Prerequisite: COMP or COMP or MATH Computer Science Sci : Concentration inequalities, PAC model, VC dimension, Rademacher complexity, convex optimization, master thesis routing protocols, gradient descent, master thesis routing protocols, boosting, kernels, support vector machines, regression and learning bounds.
Further topics selected from: Gaussian processes, online learning, regret bounds, basic neural network theory. Prerequisites: MATH or COMP or COMPMATHMATH and MATH or ECSE Restrictions: Not open to students who have taken or are taking MATH Not open to students master thesis routing protocols have taken COMP when the topic was "Statistical Learning Theory" or "Mathematical Topics for Machine Learning". Not open to students who have taken COMP when the topic was "Mathematical Foundations of Machine Learning".
Computer Science Sci : Use of computer in solving problems in discrete optimization. Linear programming and extensions, master thesis routing protocols. Network simplex method. Applications of linear programming. Vertex master thesis routing protocols. Geometry of linear programming. Implementation issues and robustness.
Students will do a project on an application of their choice. Prerequisites: COMP and MATH Computer Science Sci : Formulation, solution and applications of integer programs. Branch and bound, cutting plane, and column generation algorithms. Combinatorial optimization.
Polyhedral methods. A large emphasis will be placed on modelling. Students will select and present a case study of an application of integer programming in an area of their choice. Prerequisites: COMP or MATH Computer Science Sci : Study of elementary data structures: lists, stacks, queues, trees, hash tables, binary search trees, red-black trees, heaps.
Augmenting data structures. Sorting and selection, Recursive algorithms. Advanced data structures including binomial heaps, Fibonacci heaps, disjoint set structures, and splay trees. String algorithms. Huffman trees and suffix trees. Graph algorithms. Computer Science Sci : Introduction to mathematical concepts important across computer science, how to think mathematically, and how to write proofs. Proof techniques such as induction, contradiction, and monovariants; topics in combinatorics, graph theory, algebra, analysis, and probability; mathematical analysis of algorithms, data structures, and computational complexity.
Emphasis on the mathematical explanations for useful concepts. Restrictions: Not open to students who have majored in Mathematics or an equivalent subject, or have taken a proof-based math or computer science course within the previous two years. Not open to students who have taken COMP when the topic was "Mathematical Tools for Computer Science". Computer Science Sci : Efficient and reliable numerical algorithms in estimation and their applications. Linear models and least squares estimation.
Maximum-likelihood estimation. Kalman filtering. Adaptive estimation, GPS measurements and mathematical models for positioning. Position estimation. Fault detection and exclusion. Prerequisites: MATHMATH and COMP Computer Science Sci : Information theoretic definitions of security, master thesis routing protocols, zero-knowledge protocols, secure function evaluation protocols, cryptographic primitives, privacy amplification, error correction, quantum cryptography, quantum cryptanalysis.
Computer Science Sci : Review of the basic notions of cryptography and quantum information theory. Quantum key distribution and its proof of security.
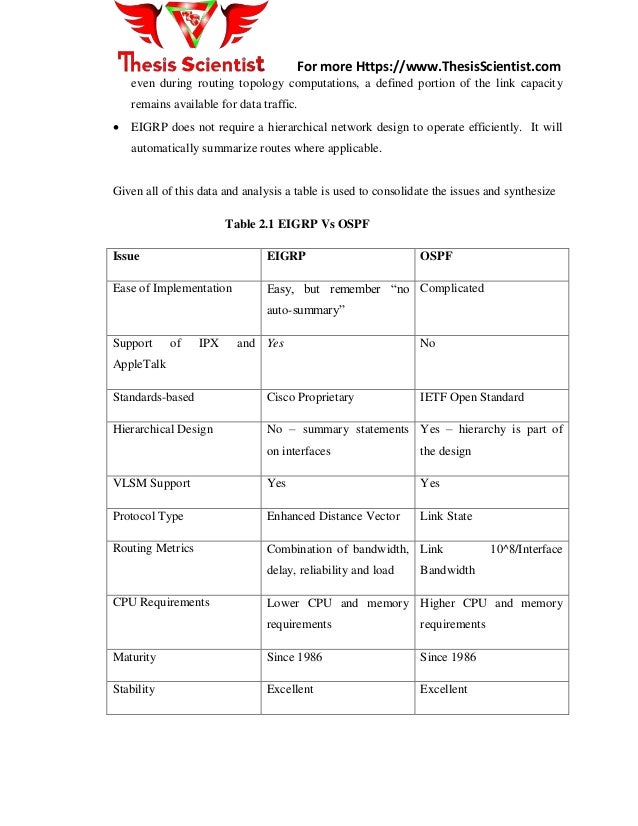
2. Link State Routing Protocols
, time: 11:03Master of Computer Science < uOttawa
Thesis and Research Topics in Computer Science. The secure and energy efficient data routing in the IOT based networks; (W3C) to promote common data formats and exchange protocols over the web. It is machine-readable information based and is built on XML technology. It Master of Engineering: 30 Credits or 10 Courses. Students earning a Master of Engineering in cybersecurity take four core courses, two Cybersecurity electives, and four technical electives. Any non pre-approved technical electives must be approved by an academic advisor prior to registering. There is no research or thesis required for this degree Aug 07, · It find its use in simulating routing protocols like IP, TCP, UDP etc. It creates a simulation environment for studying the network. The steps followed when creating a
No comments:
Post a Comment